
Do we still have control over our personal data? Nearly every piece of information about us is tied to a database these days.
To resolve this, the World Wide Web Consortium has proposed a way to help us decouple from central data registries. The method involves the adoption of decentralised identifiers that will keep us verifiable on the internet without relying on centralised parties. Sooner or later, you may find yourself owning a DID wallet to control your personal data.
Before we discuss decentralised identifiers, here’s a brief explanation of what identifiers mean.
Identifiers make anything on the internet identifiable and verifiable. We use them to locate online addresses, identification numbers and also products (i.e., through serial numbers). URLs (Uniform Resource Locator) and URIs (Uniform Resource Identifiers) are common forms of identifiers. They respectively represent the web pages you view in a browser and online resources like HTML pages or images.
However, the problem with identifiers is that the validity depends on the existence of a central registry or authorising body. The same authorities may also have the power to revoke those identifiers. For example, Facebook can use their discretion in choosing the accounts they want to suspend.
Now that you’ve learned about identifiers, decentralised identifiers, or DIDs, are a new type of globally unique identifiers. They are designed to help us remain verifiable without relying on a central authority or body. With DIDs, the holders themselves get to be the authority of their own data, by providing authentication through cryptographically secure methods like digital signatures. Users can also define the scope of use for their DIDs that is appropriate to various contexts.
According to the graphic below, a DID consists of a DID controller, a DID subject, and a DID Document. In order for the DID to be resolvable, or provide clearer information about the subject, the DID has to be recorded on a distributed data registry, such as on blockchain.
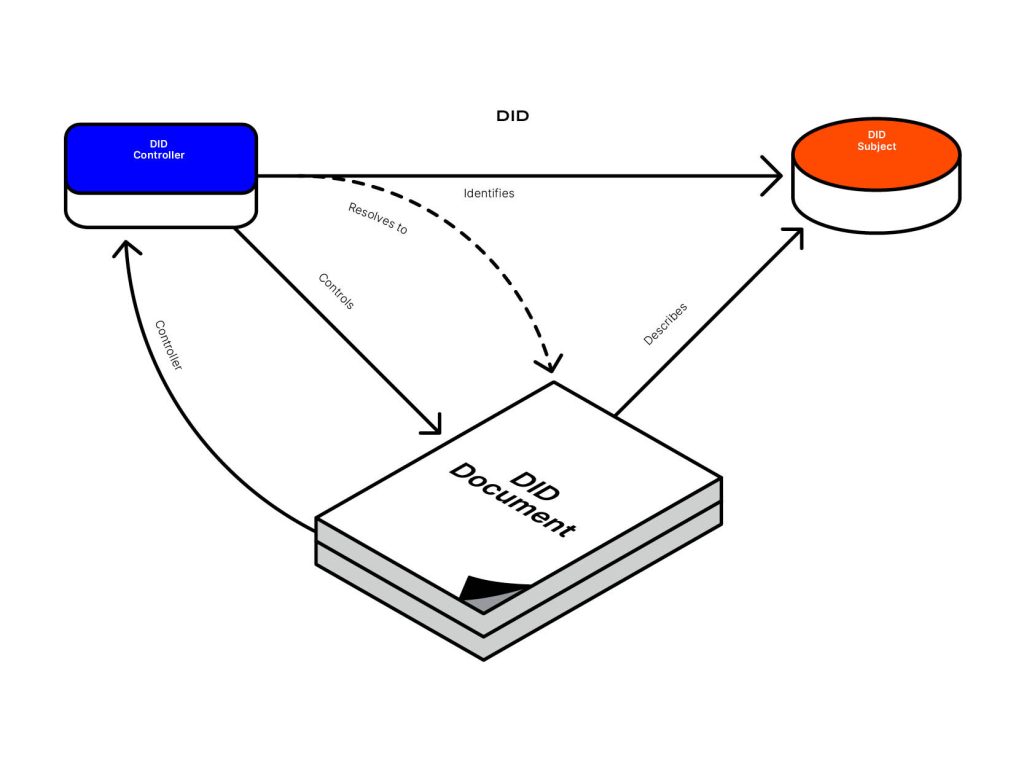
A DID document contains information associated with the subject, such as the following:
A DID controller refers to the entity that has the capability of making changes to the DID. The controller may also be the DID subject.
This refers to the subject identified by the DID and in the DID document. This could be a person, group, organisation, or physical and digital items.
To summarise, decentralised identifiers can help us improve the way we control and manage our personal data. Being in control of our personal data protects us from undesirable situations like invasion of privacy and data leakage as a result of a data breach. What’s also interesting is that DIDs are customisable. We can personalise them according to our data privacy needs and secure them through cryptography.
UKISS Technology is creating a decentralised security ecosystem that incorporates a self-sovereign identity blockchain, our multipurpose Hugware® hardware wallet, and KISS Tokens. For more details on how we plan to return control of identity and security to digital natives, read our White Paper.